In this weekly roundup, we delve into the newest updates about the much-anticipated smartphones from two industry giants: Google and Samsung. As the tech world buzzes with excitement, here’s everything you need to know about their next phones.
Apa itu kipas pintar dan bagaimana cara kerjanya?
Dalam era teknologi yang semakin maju, berbagai perangkat rumah tangga kini juga mengalami banyak inovasi. Salah satunya adalah kipas pintar. Artikel ini akan menjelaskan apa itu kipas pintar dan bagaimana cara kerjanya. Selain itu, kita juga akan membahas fitur-fitur utama yang biasanya ada pada kipas pintar serta manfaat yang bisa Anda dapatkan dari penggunaan alat ini.
Dapatkah hub digunakan bersama dengan switch?
Dalam dunia jaringan komputer, seringkali muncul pertanyaan tentang apakah hub dapat digunakan bersama dengan switch. Memahami bagaimana kedua perangkat ini bekerja dan berinteraksi sangat penting untuk membangun jaringan yang efisien dan andal. Artikel ini akan mengupas topik tersebut secara mendalam untuk membantu Anda memutuskan penggunaan terbaik bagi kedua perangkat tersebut dalam jaringan Anda.
How to Maximize the Speed of Your Internet Connection?
In a world where online activities dominate both personal and professional spheres, having a fast and reliable internet connection is no longer a luxury but a necessity. Multiple factors can affect your internet speed, from your hardware and network settings to external influences like your ISP (Internet Service Provider). This comprehensive guide will delve into various methods to maximize the speed of your internet connection, ensuring you can make the most of your online experience.
Swift and Simple Instagram Video Download
Experience the convenience of swift and simple Instagram save story, empowering users to capture and share content effortlessly. Explore the tools and techniques that facilitate quick and hassle-free content acquisition, enhancing the user experience. Discover the impact of streamlined downloads on content consumption and digital storytelling.
Video Downloader – ssyoutube.com
Downloading online videos has become increasingly important for many people. Do you often find interesting videos on YouTube that you want to save on your device? Well, the video downloader on ssyoutube.com is the practical solution for this need. This article will comprehensively discuss ssyoutube.com, a leading service for downloading videos from YouTube easily and quickly.
Cara Mudah Download Video Instagram Tanpa Aplikasi Tambahan
Instagram adalah salah satu platform media sosial yang populer untuk berbagi foto dan video. Namun, tidak semua konten bisa diunduh secara langsung dari aplikasi. Untuk Anda yang sering menemukan video menarik dan ingin menyimpannya, berikut adalah cara mudah download video Instagram tanpa perlu aplikasi tambahan.
Download YouTube Shorts with YT Video Downloader
YouTube Shorts have taken the digital world by storm, offering quick, engaging video content that’s easy to consume. However, what if you want to save these videos for offline viewing or sharing? Enter the versatile YT video downloader, a robust tool designed to help you download YouTube Shorts effortlessly.
Detailed Guide to YouTube Video Download with ssyoutube.com
Downloading videos from YouTube is made simple with the download YouTube videos feature available on ssyoutube.com. This comprehensive guide covers all aspects of using this tool to efficiently and securely download videos from YouTube.
How Use ngrok in Windows?
Ngrok is a powerful tool that allows developers to create secure tunnels to their localhost. This is especially useful for testing webhooks, APIs, and other web services in a local development environment. Using ngrok on a Windows system involves a few straightforward steps. In this guide, we’ll delve into the process, from downloading and installing ngrok to configuring and running it.
Understanding Device Repairability Scoring Systems
Device repairability scoring systems have become increasingly important in the technology industry, providing consumers with valuable information about the ease of repairing their gadgets. These scoring systems help users make informed decisions, reduce electronic waste, and promote sustainability. In this article, we will delve into the details of device repairability scoring systems, their significance, and how they are calculated.
エッジコンピューティングがもたらす産業変革:次世代テクノロジーが実現する新たなビジネスの可能性
現代のデジタル社会において、データ処理の方法は急速に進化を続けています。エッジコンピューティングは、クラウドコンピューティングの限界を超えて、データの発生源により近い場所で処理を行う革新的な技術として注目を集めています。
Regulate Fan Noise Automatically Lifehacks
Unwanted fan noise can turn an otherwise silent PC into a distracting hum, especially under light workloads. Default BIOS fan curves are often conservative—spinning fans up too quickly at low temperatures. Software solutions may help, but piecemeal tweaks rarely achieve the ideal balance between cooling and quiet. By automating fan control through coordinated BIOS settings and user-space tools, you can create dynamic cooling profiles that adjust speeds precisely to thermal demands. These lifehacks will guide you through configuring BIOS options, deploying software for fine-grained control, defining temperature-based curves, integrating multiple sensor inputs, and monitoring results to maintain a perfectly silent yet safe system.
Como desenhar uma moldura de foto com uma caneta 3D?
Desenhar uma moldura de foto com uma caneta 3D é uma maneira divertida e criativa de personalizar as suas lembranças. Com a popularidade crescente das canetas 3D, muitas pessoas estão descobrindo novas formas de arte e design. Neste guia, vamos explorar como criar uma moldura de foto única utilizando uma caneta 3D.
Find the Best Phone Cases for Protection
Your smartphone is likely one of your most essential and frequently used devices, so keeping it safe from accidental drops, scratches, and impacts is a priority. A durable, high-quality phone case can be the difference between a shattered screen and a fully functional device after an unfortunate mishap. With countless options available, it can be challenging to find the best case for maximum protection. This guide will help you choose the right phone case to safeguard your phone.
Você pode criar uma cúpula de abajur com uma caneta 3D?
As canetas 3D têm revolucionado o mundo do artesanato, permitindo que as pessoas criem uma variedade de objetos tridimensionais com facilidade e precisão. Mas você sabia que também é possível criar uma cúpula de abajur usando uma caneta 3D? Nesse artigo, vamos explorar os materiais, os passos necessários e algumas dicas para que você possa criar uma cúpula de abajur única e personalizada.
Automate Travel Details in Shortcuts Lifehacks
Planning a trip often means juggling airline confirmations, hotel bookings, rental car codes, and transit directions across multiple apps. With Shortcuts on your device, you can automate the extraction and display of all your travel details in one seamless routine. By defining a single shortcut that pulls data from your calendar, email, and wallet, you eliminate manual lookups and reduce last-minute stress. In this post, we’ll explore why automating travel itineraries matters, show you how to aggregate trip data in Shortcuts, demonstrate chaining actions to launch your itinerary at a tap, and share best practices for building reliable travel workflows.
IPFS gana tracción en proyectos de almacenamiento descentralizado
En la era digital actual, la necesidad de soluciones de almacenamiento eficientes y seguras es más crucial que nunca. Con el crecimiento exponencial de datos, el almacenamiento descentralizado se ha convertido en una alternativa viable a las soluciones tradicionales. IPFS (InterPlanetary File System) ha emergido como un pionero en este ámbito, ganando tracción en numerosos proyectos de almacenamiento descentralizado.
Apple vs. The Competition: A Comprehensive Overview
Apple Inc. has been a dominant force in the technology industry for decades. Known for its innovative products and premium branding, the company often finds itself in intense competition with other tech giants. This article delves into the various facets of the ‘Apple vs.’ landscape, examining its key competitors, market strategies, and the impact on consumers.
Reset a Vizio Soundbar: Soft or Factory Reset + Troubleshooting
When your Vizio soundbar is not functioning properly, performing a reset can often solve the issue. There are two main types of resets you can try: soft reset and factory reset. Each method serves a different purpose and can help address various problems you may encounter.
Can I Use a USB Hub to Connect Multiple Gaming Peripherals to My Xbox?
As gaming enthusiasts continue to expand their setups, a common question arises: can I use a USB hub to connect multiple gaming peripherals to my Xbox? The answer is nuanced, depending largely on the type of peripherals being connected and the specific Xbox model in question. This article delves into the compatibility, advantages, and limitations of using USB hubs with Xbox consoles, providing you with the necessary information to make an informed decision.
Opendoor’s Governance Reset with a New CEO and Chairman: Will Housing Tech Rebound?
In the rapidly evolving world of real estate technology, Opendoor has emerged as a significant player, revolutionizing how people buy and sell homes. However, recent leadership changes have sparked conversations about the company’s direction and the broader implications for the housing tech industry. This article delves into Opendoor’s governance reset with a new CEO and chairman, examining the potential for a rebound in housing tech.
حلول بريد إلكتروني مؤسسية تضيف توقيعات DKIM وDMARC تلقائيًا للمؤسسات الصغيرة
في عالم الأعمال اليوم، يعد البريد الإلكتروني أداة حيوية تساهم في التواصل الفعال بين المؤسسات وعملائها. لكن مع تزايد التهديدات السيبرانية، أصبح من الضروري أن تتبنى المؤسسات الصغيرة حلولًا متقدمة تضمن أمان رسائلها الإلكترونية. واحدة من هذه الحلول هي استخدام توقيعات DKIM وDMARC.
AI Models Mapping Hidden Galaxies Behind the Milky Way’s Dust Clouds
The vastness of the universe holds secrets beyond our imagination, and one of the most intriguing challenges faced by astronomers is mapping the hidden galaxies obscured by the Milky Way’s dust clouds. The Milky Way, with its dense clouds of dust and gas, often obstructs our view of the universe and the countless galaxies that reside beyond it. However, advancements in artificial intelligence (AI) are opening new avenues for exploration. This article delves into how AI models are being employed to identify and map these elusive galaxies, revealing insights that could reshape our understanding of the cosmos.
Spotify Piloting AI Powered Festival Playlist Creators in U.S. Regions
In a groundbreaking move that could redefine the music festival experience, Spotify is piloting an innovative AI-powered feature designed to craft personalized festival playlists for users across various U.S. regions. This initiative aims to bridge the gap between music lovers and live events, allowing fans to immerse themselves in tailored soundtracks that resonate with their individual tastes and local vibes.
Best 32 Inch TV: Top Picks for Crisp Picture Quality and Smart Features
When it comes to picking a new TV, size does matter, but bigger isn’t always better. A 32-inch TV is perfect for smaller rooms, dorms, or even as a secondary TV in bedrooms and kitchens. Despite their compact size, many 32-inch TVs offer high-definition picture quality and smart features that rival their larger counterparts. Let’s dive into some of the best options available on the market today.
What Should I Do If My USB Hub Stops Working?
USB hubs are essential devices for expanding the number of USB ports available on your computer, enabling you to connect multiple devices simultaneously. However, like any technology, they can sometimes fail, causing frustration. If your USB hub stops working, it’s important to understand the potential causes and effective solutions. This guide will walk you through troubleshooting steps and maintenance tips to get your USB hub back in working order.
How to Extend the Free Trial Period on Mac Applications
Free trials are a great way to explore the features and capabilities of an application before committing to a purchase. Generally, these trials last anywhere from a few days to a month. However, many users wonder if there are ways to extend this period without breaking any rules.
Easily Block Websites on an iPad with Screen Time
With the increase in internet usage, it is crucial for parents and guardians to control the content accessible to children. Apple’s Screen Time provides a robust solution to easily block websites on an iPad, ensuring a safe online environment. This article will guide you through the steps to set up and use Screen Time for blocking websites effectively.
How do I prevent signal interference when using a USB hub?
USB hubs have become essential components in modern computer setups, facilitating the connection of multiple devices to a single USB port. However, users often encounter issues with signal interference that can hamper performance. Understanding how to prevent such interference is crucial for optimal functioning. In this article, we will explore effective strategies to maintain a seamless connection while using a USB hub.
What can cause a USB to VGA adapter to overheat?
A USB to VGA adapter is a device that allows you to connect a VGA monitor or projector to a computer using a USB port. These adapters are particularly useful in expanding your display capabilities, enabling you to work on multiple screens simultaneously. However, like any electronic device, they can experience issues, including overheating. In this article, we will explore the common causes of overheating in USB to VGA adapters and how to mitigate these risks.
Does a Samsung Factory Reset Delete Everything?
A factory reset, also known as a master reset, is a process of restoring your Samsung device to its original system state by erasing all the data stored on the device. This includes all installed apps, user data, and system settings.
Cloud Collaboration: Kolaborasi Tim yang Efisien
Kolaborasi tim menjadi lebih penting dalam lingkungan kerja modern, terutama dengan lebih banyak tim yang bekerja secara remote dan terpisah. Dalam artikel ini, kita akan membahas bagaimana layanan kolaborasi cloud memungkinkan tim untuk bekerja bersama secara efisien, berbagi file, dan berkomunikasi tanpa batas geografis.
Is there a recommended USB cable length for VGA adapters?
VGA (Video Graphics Array) adapters are commonly used to connect computers to monitors, especially older models. However, in today’s digital world, many devices are equipped with USB ports, leading to the need for USB to VGA adapters. These adapters facilitate the connection between modern devices and traditional displays, providing a bridge between differing technologies.
Network Function Virtualization (NFV): Increasing Network Agility
What if networks could adapt as quickly as the applications they support? Network Function Virtualization (NFV) is revolutionizing how networks operate by decoupling hardware from software. This flexibility allows for rapid deployment and adjustment of network functions on a virtualized infrastructure, enabling service providers to enhance agility and efficiency. As networks evolve to meet modern demands, NFV is the key to unlocking next-level performance and innovation.
Multi-factor Authentication (MFA): Strengthening Access Control
Securing access to systems and data has never been more critical, and Multi-factor Authentication (MFA) offers a robust solution. By requiring users to verify their identity through multiple methods, such as a password, a fingerprint, or a one-time code, MFA significantly reduces the risk of unauthorized access. This layered approach to security enhances protection for sensitive information and systems, fortifying defenses against cyber threats.
Aerospace Engineering: Teknologi Penerbangan dan Antariksa
Energi bersih adalah kunci dalam mengurangi polusi dan ketergantungan pada bahan bakar fosil. Artikel ini akan mengulas berbagai solusi dalam mengadopsi energi bersih, mulai dari panel surya hingga teknologi tenaga angin dan hidro. Pembaca akan diajak untuk memahami manfaat dan tantangan dalam mempercepat transisi menuju sumber energi yang lebih ramah lingkungan dan berkelanjutan untuk masa depan planet kita.
Microservices Architecture: Building Agile and Scalable Systems
Microservices architecture redefines how applications are built, focusing on modular, loosely coupled components that communicate via APIs. This approach offers unparalleled agility and scalability, allowing development teams to deploy and update individual services independently. By breaking down monolithic systems into smaller, manageable units, organizations can achieve faster development cycles, increased reliability, and a more dynamic response to changing business needs.
Edge Computing Applications: Real-time Data Processing
The edge of the network is transforming into a powerhouse of real-time data processing. Edge computing applications bring computation and data storage closer to data sources, enabling faster response times and reduced latency. This shift is revolutionizing industries such as healthcare, manufacturing, and transportation by empowering them to process data at the source, facilitating immediate decision-making, and unlocking new levels of efficiency and innovation.
Apa yang dimaksud dengan zonasi kipas dalam pendinginan pusat data?
Pengelolaan pusat data yang efektif memerlukan strategi pendinginan yang canggih untuk menjaga suhu optimal perangkat keras dan memastikan kinerja sistem tetap optimal. Salah satu teknik yang banyak digunakan adalah zonasi kipas atau fan zoning. Artikel ini akan membahas apa yang dimaksud dengan zonasi kipas, bagaimana cara kerjanya, serta manfaat yang ditawarkannya.
Data Center Modernization: Improving Infrastructure Efficiency
Gone are the days of static, outdated data centers. Modernization is key to ensuring infrastructure efficiency, performance, and security in today’s digital landscape. By embracing advanced technologies like virtualization, cloud integration, and software-defined solutions, data centers can optimize resource utilization and reduce costs. This evolution enables organizations to respond swiftly to market demands, streamline operations, and deliver exceptional customer experiences.
Virtual Reality Therapy: Terapi Berbasis Realitas Virtual
Inovasi dalam energi terbarukan menjadi kunci dalam mengatasi tantangan perubahan iklim dan keberlanjutan energi. Artikel ini akan mengulas berbagai teknologi terbaru dalam energi terbarukan, seperti baterai yang lebih efisien, turbin angin yang lebih besar, dan panel surya yang lebih hemat biaya. Dari pengembangan teknologi hingga implementasi kebijakan, pembaca akan diperkenalkan dengan upaya-upaya terkini dalam mempercepat adopsi energi bersih untuk menciptakan masa depan yang lebih berkelanjutan bagi bumi kita.
Software-Defined Networking (SDN): Enhancing Network Management
Envision a network that dynamically adjusts itself based on changing conditions and requirements. That’s the world of Software-Defined Networking (SDN), where network control is separated from hardware and managed centrally. By enabling programmable, agile networks, SDN enhances management efficiency and allows for rapid deployment of new services. This transformative approach paves the way for improved scalability, performance, and cost-effectiveness.
Ekosistem Keamanan Siber Indonesia: Kolaborasi Pemerintah, Industri, dan Akademia
Keamanan siber telah menjadi pilar utama dalam menjaga kedaulatan dan stabilitas digital suatu negara. Di Indonesia, ancaman siber terus berkembang, mulai dari serangan ransomware terhadap infrastruktur publik hingga pencurian data pribadi pengguna. Untuk menghadapi kompleksitas tersebut, upaya terkoordinasi antara pemerintah, industri, dan dunia akademia tidak lagi bisa ditunda. Kolaborasi strategis dan sinergi lintas sektor menjadi kunci membangun ekosistem keamanan siber nasional yang tangguh, adaptif, dan berkelanjutan.
Bagaimana cara mengatasi fluktuasi kecepatan kipas?
Pernak-pernik teknologi modern rumahan sering kali menghadapi tantangan teknis yang membuat pengguna bingung. Salah satu masalah umum yang sering muncul adalah fluktuasi kecepatan kipas. Fluktuasi kecepatan kipas tidak hanya mengurangi kenyamanan pengguna, tetapi juga dapat mempercepat keausan perangkat itu sendiri. Artikel ini akan membahas langkah-langkah yang bisa Anda ambil untuk mengatasi masalah ini dengan efektif.
How to Log Out of Viber on iPhone or iPad?
Viber is a popular messaging app that allows users to send text messages, make voice calls, and share multimedia. Sometimes, you might need to log out of Viber for various reasons, such as privacy concerns or switching accounts. If you are using an iPhone or iPad, logging out of Viber may not be as straightforward as it is on some other devices. In this guide, we will walk you through the steps to log out of Viber on your iOS device.
Apa itu kipas aliran campuran dan apa kelebihannya?
Kipas aliran campuran adalah salah satu jenis kipas yang menggabungkan karakteristik kipas aksial dan kipas sentrifugal. Kipas ini dirancang untuk menghasilkan aliran udara yang kuat dengan tekanan yang lebih tinggi dibandingkan dengan kipas aksial dan biaya energi yang lebih rendah daripada kipas sentrifugal. Kipas aliran campuran sering digunakan dalam berbagai aplikasi industri karena kinerjanya yang efisien dan fleksibilitasnya.
How to Change Application Permissions on a Mac
Changing application permissions on a Mac is a crucial task for maintaining security and control over your applications. Permissions determine what an application can access, including files, folders, and hardware components like the camera and microphone. In this article, we’ll guide you through the steps to change application permissions on your Mac effectively.
How to Set up a Computer?
Setting up a new computer can seem daunting, especially if you are not tech-savvy. Fear not! This guide will walk you through each step to ensure you get your computer up and running with ease. From hardware setup to software installation, we’ve got you covered.
How to Connect DJ Mixers to a Laptop?
For aspiring and professional DJs, connecting a DJ mixer to a laptop is essential for creating high-quality mixes, performing live, and recording sets. This guide will walk you through the steps to successfully connect your DJ mixer to a laptop, ensuring a smooth and efficient setup.
Neurotechnology: Teknologi Otak dan Saraf Manusia
Neurotechnology, yang kini semakin berkembang pesat, mengeksplorasi hubungan antara teknologi dan otak manusia. Artikel ini akan mengulas bagaimana neurotechnology mengubah paradigma dalam bidang kesehatan, pendidikan, dan bahkan hiburan. Dari Brain-Computer Interface (BCI) hingga pengobatan neurologis inovatif, teknologi ini menjanjikan potensi luar biasa untuk meningkatkan kualitas hidup manusia.
How to Clean a Computer Monitor/LCD Screen?
Keeping your computer monitor or LCD screen clean is crucial not only for clarity and aesthetic appeal but also for prolonging the life of your device. Dust, fingerprints, and smudges can all contribute to a less than optimal screen display. Here’s a comprehensive guide to help you clean your computer monitor or LCD screen effectively.
Dapatkah saya menggunakan hub USB dengan TV pintar saya?
Di era digital ini, TV pintar menjadi semakin populer di rumah-rumah banyak orang. TV pintar memberikan akses ke berbagai konten digital dan kemampuan untuk terhubung dengan berbagai perangkat. Salah satu pertanyaan umum yang sering muncul adalah, “Dapatkah saya menggunakan hub USB dengan TV pintar saya?” Jawabannya adalah ya, Anda bisa menggunakan hub USB dengan TV pintar Anda. Pada artikel ini, kita akan menggali lebih dalam tentang bagaimana cara menggunakan hub USB dengan TV pintar dan manfaat yang Anda dapatkan dari perangkat tersebut.
Ways to Connect a Soundbar to a Windows Computer
Enhancing the audio experience on your Windows computer can significantly improve your workflow and entertainment experiences. One of the most effective ways to do this is by connecting a soundbar to your computer. Soundbars provide superior sound quality compared to built-in computer speakers, and they are relatively easy to set up. In this article, we’ll explore different ways you can connect a soundbar to your Windows computer.
How to Clean a PC Fan?
Keeping your PC fan clean is crucial for the optimal performance of your computer. A dusty or clogged fan can lead to overheating, reduced performance, and even hardware damage. In this guide, we will walk you through the steps to clean your PC fan efficiently and safely.
How to Record Sound Produced by Your Sound Card?
Recording sound directly from your sound card can be essential for various needs, such as capturing audio from streaming services, recording VoIP calls, or creating tutorials. Here’s a comprehensive guide on how to record sound produced by your sound card effectively.
Cognitive Science: Ilmu Kognitif dalam Pemahaman Manusia
Konservasi keanekaragaman hayati menjadi semakin penting di tengah meningkatnya ancaman terhadap satwa liar. Artikel ini akan mengulas berbagai strategi dan upaya dalam melindungi flora dan fauna yang terancam punah serta menjaga ekosistem mereka. Dari pembentukan kawasan konservasi hingga upaya pemulihan spesies yang terancam, pembaca akan diajak untuk memahami pentingnya pelestarian keanekaragaman hayati bagi keseimbangan ekologi dan kelangsungan hidup manusia.
How to Arrange Stickers on a Laptop?
Decorating your laptop with stickers can be a fun and creative way to showcase your personality. However, arranging these stickers in an appealing manner requires some thought and planning. This guide provides you with various strategies to ensure your laptop screams ‘you’ without looking cluttered or messy.
How to Factory Reset AirPods?
AirPods have become an essential accessory for many people, providing a seamless and wireless audio experience. However, like any electronic device, they can encounter issues that might require a factory reset. This article will guide you through the steps to factory reset your AirPods, ensuring they function properly.
Bagaimana cara mengetahui apakah port USB-C saya mendukung keluaran video?
Port USB-C semakin populer digunakan di berbagai perangkat, mulai dari laptop, smartphone, hingga tablet. Salah satu fitur yang paling dicari adalah kemampuan keluaran video. Tetapi bagaimana cara mengetahui apakah port USB-C di perangkat Anda mendukung keluaran video? Artikel ini akan membantu Anda mengidentifikasi kemampuan port USB-C Anda.
How to Clean a Computer Mouse?
In today’s digital age, a computer mouse is an indispensable tool in our day-to-day interactions with technology. Over time, dust, grime, and other debris can accumulate on your mouse, affecting performance and hygiene. Cleaning your computer mouse regularly helps maintain its efficiency and prolongs its lifespan. In this article, we will provide a detailed, step-by-step guide on how to clean a computer mouse effectively.
How to Discharge a CRT Monitor?
Cathode Ray Tube (CRT) monitors, though largely replaced by modern flat panel displays, still exist in some households and workplaces. If you’re a hobbyist, repair technician, or even someone trying to safely dispose of old electronics, you must know that CRT monitors store high voltage even when they’re unplugged. Discharging them safely is critical to avoid severe electric shock. This guide will provide a thorough step-by-step process on how to discharge a CRT monitor.
Clean Water Technology: Teknologi Air Bersih untuk Semua
Arsitektur berkelanjutan menjadi kunci dalam menciptakan lingkungan binaan yang ramah lingkungan dan berdaya guna. Artikel ini akan membahas prinsip-prinsip arsitektur berkelanjutan serta berbagai teknologi dan material yang digunakan dalam pembangunan bangunan hijau. Dari desain pasif energi hingga pemanfaatan sumber energi terbarukan, pembaca akan diperkenalkan dengan pendekatan inovatif dalam merancang bangunan yang mengurangi jejak lingkungan dan mendukung kesejahteraan penghuninya.
Disaster Recovery Planning: Business Continuity
Disaster recovery planning is essential for ensuring business continuity during unforeseen events. By preparing for potential disruptions, organizations can minimize downtime and loss. This article delves into the components of effective disaster recovery planning, including risk assessment, backup strategies, and recovery processes, to help businesses maintain operations and resilience.
Disaster Recovery Planning: Business Continuity
Disaster recovery planning is essential for ensuring business continuity during unforeseen events. By preparing for potential disruptions, organizations can minimize downtime and loss. This article delves into the components of effective disaster recovery planning, including risk assessment, backup strategies, and recovery processes, to help businesses maintain operations and resilience.
How to Fix the Low Volume on Your AirPods?
AirPods offer convenience and superior sound quality, but every gadget has its occasional hiccup. One common issue users face is low volume. If you’re experiencing this problem, don’t worry—you’ve come to the right place. This article will provide step-by-step solutions to help you resolve the low volume issue on your AirPods.
How to Use Headphones on an iPhone 7?
The iPhone 7, launched by Apple in 2016, marked a significant change in the way users interact with their devices by eliminating the traditional 3.5mm headphone jack. This move caused a stir among users who were accustomed to using wired headphones. However, Apple provided alternative options to ensure that users still enjoy high-quality audio experiences with their iPhone 7.
Bagaimana cara memecahkan masalah hub jaringan?
Kelancaran jaringan sangat penting dalam menjalankan bisnis atau aktivitas sehari-hari, dan hub jaringan adalah komponen kunci dari sistem ini. Namun, terkadang masalah dapat muncul yang mengganggu konektivitas. Mengetahui cara memecahkan masalah hub jaringan dapat membantu meminimalisir downtime dan mempertahankan produktivitas.
Understanding How Hackers Bypass CAPTCHA Systems
CAPTCHA, which stands for Completely Automated Public Turing test to tell Computers and Humans Apart, is a widely used security measure designed to prevent automated bots from accessing websites and services. By presenting challenges that are easy for humans but difficult for machines, CAPTCHAs help protect against spam, brute-force attacks, and other malicious activities.
Can I use a USB to VGA adapter with a USB hub?
In today’s tech-driven world, the need for versatile connectivity options is paramount. One common question that often arises is whether a USB to VGA adapter can be used with a USB hub. This article aims to clarify this question and provide insights into how these devices work together.
The Use of Drones in Archaeological Exploration: Revolutionizing Ancient Discovery
In recent years, the integration of drone technology into archaeological research has fundamentally transformed how we discover, document, and understand ancient sites. This technological revolution has opened up new possibilities for archaeologists worldwide, providing unprecedented access to archaeological sites and delivering detailed insights that were previously impossible to obtain.
Can I Charge Devices Like Phones and Tablets Using a USB Hub?
As our world becomes increasingly digital, the need to keep our devices charged is more crucial than ever. With multiple devices, from smartphones to tablets, finding the right charging solution can be a significant challenge. A common question many users have is whether they can charge their devices using a USB hub. This article will explore the relationship between USB hubs and charging capabilities, helping you understand this technology better.
The Future of Artificial Intelligence: How AI is Shaping Everyday Life
Artificial Intelligence (AI) is no longer a concept confined to science fiction. It has rapidly permeated various aspects of our daily lives, fundamentally transforming how we live, work, and interact. This article delves into how AI is shaping the present and what the future holds for this groundbreaking technology.
Are HD webcams compatible with all laptops?
The rise of remote work, online education, and virtual meetings has propelled the demand for high-definition (HD) webcams. Consumers often wonder, are HD webcams compatible with all laptops? In this article, we will delve into the compatibility issues, technical requirements, and how to ensure your laptop is ready to support an HD webcam.
iPhone Check In Feature: Enhancing Safety and Peace of Mind
The iPhone Check In feature is a cutting-edge function designed to improve safety and connectivity for users. This feature, part of Apple’s expanded toolkit, allows users to notify predetermined contacts of their status, ensuring loved ones are informed in case of emergencies.
How to Adjust Your Mouse Speed, Sensitivity, & More?
Your mouse is one of the most important peripherals for navigating and interacting with your computer. Adjusting the mouse speed, sensitivity, and other settings can greatly enhance your productivity and comfort. Whether you’re a gamer, a graphic designer, or just a regular user, fine-tuning these settings can make a world of difference.
IT Asset Management: Resource Optimization
IT asset management focuses on tracking and optimizing the use of technology assets within an organization. Proper management helps reduce costs, improve efficiency, and enhance decision-making. This article explores the principles of IT asset management, including inventory tracking, lifecycle management, and resource optimization, providing insights into how businesses can maximize the value of their IT investments.
Layanan Story Viewer untuk Instagram Tanpa Diketahui
Apakah Anda pernah penasaran ingin melihat Instagram stories seseorang tanpa ingin mereka tahu? Jika iya, maka layanan story viewer dari anonyig.com adalah solusi yang tepat untuk Anda. Layanan ini memungkinkan Anda untuk melihat stories tanpa meninggalkan jejak.
Meningkatkan Pengalaman Melihat Cerita Instagram dengan Instagram Story Viewer
Jika Anda sering menggunakan Instagram, Anda mungkin penasaran dengan cerita pengguna lain tanpa ingin diketahui oleh mereka. Untungnya, ada layanan yang dapat membantu Anda tetap anonim saat melihat cerita Instagram, yaitu instagram story viewer. Situs ini menawarkan solusi praktis untuk melihat cerita Instagram tanpa memberi tahu pemilik cerita.
Cara Terbaik Mengunduh Video Instagram dengan Mudah dan Cepat
Mengunduh video dari Instagram kini semakin mudah dengan adanya instagram video downloader yang bisa digunakan secara online. Website ini menyediakan layanan cepat dan efisien untuk mendownload video dari Instagram tanpa perlu menginstal aplikasi tambahan. Dengan antarmuka yang sederhana, pengguna dapat dengan mudah menempelkan tautan video yang ingin diunduh dan mendapatkan hasilnya dalam hitungan detik.
How to Change Your Apple ID Password
Changing your Apple ID password periodically is essential for maintaining the security of your account. A strong password helps protect your personal information, prevent unauthorized access, and ensure the safety of your data.
Instagram Video Downloader
Instagram is one of the most popular social media platforms today, with millions of users sharing photos and videos daily. However, downloading videos from Instagram isn\’t straightforward. Whether you want to save a video for offline viewing or repurpose content, this guide will walk you through the process of using an Instagram video downloader.
The Ultimate Guide to Downloading Instagram Reels
Instagram Reels have become a popular feature, allowing users to create short, engaging videos. However, one common question is how to download these Reels for offline viewing. In this guide, we will explore various methods to download Instagram Reels efficiently.
Instagram Video Download: How to Save Videos Easily
Instagram is one of the most popular social media platforms, and it’s packed with engaging video content. Whether it’s a funny clip, an inspiring story, or a tutorial, there are many videos you’d love to save. However, Instagram does not offer a built-in option for downloading videos. This article will guide you through the various methods you can use to download Instagram video easily.
How to Check CPU Temp on a Windows 11 PC?
Keeping tabs on your CPU temperature is crucial to maintaining your Windows 11 PC’s performance and longevity. Overheating can lead to significant hardware issues or reduced computing efficiency. This article will guide you through various methods to check the CPU temp on a Windows 11 PC.
Why Alphabet’s Antitrust Scare Faded and the Stock Rerated to Megacap Status
In the dynamic world of technology, few companies have had as profound an impact as Alphabet Inc. (GOOGL). The parent company of Google has shaped the digital landscape, but its journey has not been without challenges. Recently, Alphabet faced significant antitrust scrutiny that raised concerns among investors and analysts alike. However, as the dust settled, the antitrust scare began to fade, and with it, the stock was rerated to megacap status. This article delves into the factors behind this transformation, the implications for Alphabet’s future, and what it means for investors in the tech sector.
Kominfo Buat Standar Keamanan Nasional untuk Aplikasi Transportasi Daring
Di era digital yang terus berkembang, aplikasi transportasi daring menjadi salah satu solusi yang sangat dibutuhkan oleh masyarakat. Namun, dengan meningkatnya penggunaan aplikasi ini, muncul pula tantangan terkait keamanan data dan privasi pengguna. Menyadari pentingnya hal ini, Kementerian Komunikasi dan Informatika (Kominfo) Indonesia telah mengambil langkah strategis dengan menetapkan standar keamanan nasional untuk aplikasi transportasi daring.
Meta Adds Workplace Well-Being Metrics into Enterprise VR Tools
In an era where technology is rapidly transforming the workplace, Meta has taken a significant step forward by incorporating workplace well-being metrics into its enterprise virtual reality (VR) tools. This innovative development aims to create a more supportive and health-conscious work environment, fostering not only productivity but also employee satisfaction. In this article, we will delve into the details of this integration, exploring its implications for businesses and employees alike.
NASA Launches AI-Powered Orbital Debris Detection Satellites
As humanity continues to expand its presence in space, the issue of orbital debris becomes increasingly pressing. Recognizing this challenge, NASA has taken a significant step forward by launching AI-powered satellites aimed at detecting and managing this debris. This article delves into the implications of this groundbreaking technology, its historical context, future predictions, and its broader significance for space exploration.
Telecom Companies Face Fines Over Failure to Meet Rural Broadband Expansion Targets
In an era where connectivity is paramount, the disparity between urban and rural broadband access has become increasingly evident. As telecom companies strive to bridge this digital divide, recent developments have unveiled a pressing issue: many of these companies are facing substantial fines for their failure to meet mandated rural broadband expansion targets. This article delves into the implications of these fines, the historical context that led to current regulations, and what the future may hold for rural broadband access.
Tesla Gigafactory New York Adding AI Solar Panel Optimization Line
Tesla has continually positioned itself as a leader in sustainable energy solutions, and its Gigafactory in New York is a testament to this commitment. As part of its ongoing efforts to innovate and enhance productivity, Tesla has recently announced the addition of an AI solar panel optimization line at this facility. This development not only reinforces Tesla’s dedication to renewable energy but also highlights the growing intersection of artificial intelligence (AI) and solar technology.
Meta Rolls Out Parental AI Controls on U.S. Instagram Accounts
In an era where social media plays a crucial role in the daily lives of millions, especially the younger generation, the importance of safety and parental guidance cannot be overstated. Meta, formerly known as Facebook, has taken a significant step forward by rolling out parental AI controls on Instagram accounts in the United States. This initiative aims to empower parents to oversee their children’s online interactions while fostering a safer social media environment.
Best YouTube to MP3 Converter: Complete Guide to Free Online Audio Downloads
YouTube to MP3 conversion has become an essential tool for millions of users worldwide who want to extract audio content from video files. This technology allows you to transform YouTube videos into downloadable MP3 audio files, enabling offline listening and convenient access to your favorite content across various devices.
Apple TV+ Expands into Generative Animation Projects
Apple TV+, a leader in innovative streaming content, is making significant strides into the world of generative animation projects. This move marks a pivotal moment not only for Apple but also for the animation industry as a whole. With the advancement of artificial intelligence and machine learning, generative animation offers a unique blend of technology and creativity, providing a fresh avenue for storytelling.
Asana Launches Predictive Task Deadlines with AI
In the ever-evolving landscape of project management, Asana has taken a significant leap forward by launching its innovative feature of predictive task deadlines powered by artificial intelligence (AI). This groundbreaking enhancement is set to revolutionize the way teams manage their workloads, prioritize tasks, and meet project deadlines. In this article, we will explore the implications of this new feature, its historical context, potential future developments, and the myriad ways it can enhance productivity.
Connected Home Technology Adoption Reaches 75% of American Households
The rise of connected home technology has been nothing short of revolutionary. With a staggering 75% of American households now embracing this smart technology, the landscape of home automation and IoT (Internet of Things) is rapidly changing. In this article, we will delve into the reasons behind this surge, the benefits and challenges it presents, and what the future holds for connected home technology in the United States.
Green Hydrogen Production Achieves Cost Parity with Fossil Fuels
As the world grapples with the pressing challenges of climate change and the need for sustainable energy solutions, green hydrogen has emerged as a potential game-changer in the energy landscape. Recent advancements in technology and increased investments have led to a significant milestone: green hydrogen production has achieved cost parity with fossil fuels. This article explores the significance of this development, its historical context, current status, and future implications.
Instagram Story Viewer: The Ultimate Guide to Anonymous Viewing and Privacy Tools
In today’s digital landscape, Instagram Stories have become an integral part of social media communication, with over 500 million users engaging with this feature daily. However, the desire for privacy and anonymous viewing has led to the emergence of Instagram story viewer tools that promise discretion while browsing content.
How Should I Safely Unplug and Clean Peripherals?
In our technology-driven world, peripherals are essential components that enhance our computing experience. Whether it’s a mouse, keyboard, printer, or external hard drive, keeping these devices clean and functioning properly is crucial. However, disconnecting and cleaning them can sometimes be a daunting task. This article will guide you through the process of safely unplugging and cleaning your peripherals while ensuring their longevity.
The Ultimate Guide to Instagram Story Viewers: Everything You Need to Know
In today’s digital landscape, Instagram Stories have revolutionized how we share moments and connect with our audience. With over 500 million daily active users engaging with Stories, understanding who views your content has become increasingly important. Whether you’re a content creator, business owner, or casual user, knowing the ins and outs of Instagram story viewer functionality can significantly impact your social media strategy.
Performance Metrics Show Up to 44 Percent FPS Boost
In the world of gaming and high-performance graphics, performance metrics play a critical role in understanding and improving system efficiency. Recent studies and updates have shown that performance metrics can lead to a significant FPS boost (frames per second) of up to 44 percent. This article delves into the implications of these metrics, their importance, and how they affect our overall gaming experience.
Why Cloud Migration Often Overruns Budget Expectations
Cloud migration is the process of moving data, applications, and other business elements from on-premises infrastructure to cloud-based services. This transition promises numerous benefits including scalability, flexibility, and cost efficiency. However, many organizations find themselves facing unexpected costs during this migration process. In this article, we will delve into the reasons behind these budget overruns and explore effective strategies for managing expectations and costs.
Agentic Business Process Management: Revolutionary Insights and Strategic Implementation
In today’s rapidly evolving business landscape, organizations are constantly seeking innovative approaches to streamline their operations and enhance efficiency. Agentic Business Process Management (ABPM) has emerged as a groundbreaking methodology that combines traditional BPM principles with artificial intelligence and autonomous agent systems. This comprehensive guide delves into the intricate aspects of ABPM, providing valuable insights for businesses looking to transform their operational framework.
RFK Jr.’s Organic Advocacy: Catalyst for Unforeseen Political Alliances
Robert F. Kennedy Jr., widely recognized for his environmental activism and staunch advocacy for public health, has been a prominent figure in American politics for decades. His organic approach to advocacy—emphasizing grassroots movements, community engagement, and transparent communication—has not only garnered widespread support but has also led to the formation of unexpected political alliances. This article delves into the dynamics of RFK Jr.’s advocacy and explores the unforeseen partnerships that have emerged as a result.
How to Change from HEIC to JPG: A Comprehensive Guide
Converting HEIC to JPG is a common task for many users, especially when dealing with image files from newer Apple devices. If you’re looking for a reliable and user-friendly way to change from HEIC to JPG, this comprehensive guide is for you. In this article, we will explore the differences between HEIC and JPG formats, discuss the best methods for conversion, and provide detailed step-by-step instructions to help you through the process.
Moon vs. Mars: The Ongoing Debate on Prioritizing US Space Exploration Missions
The future of US space exploration has reached a pivotal moment, with policymakers and space enthusiasts alike debating whether the nation’s next ambitious mission should target the Moon or the Red Planet, Mars. This debate centers around various factors, including scientific potential, cost, technological challenges, and the broader implications for humanity’s future in space.
Understanding the Role of Oracles in Computer Science and Their Practical Applications
In the ever-evolving landscape of computer science, oracles play a crucial role, bridging the gap between deterministic algorithms and the unpredictable nature of real-world data. This article delves into the concept of oracles, exploring their fundamental purpose, practical applications, and the impact they have on various technological advancements.
Exploring the Unique Features and Impact of sssTwitter
sssTwitter has emerged as a unique and exciting addition to the world of social media, offering a fresh take on the traditional microblogging experience. This article delves into the distinctive features of sssTwitter, its impact on the digital landscape, and how it stands out from other platforms like Twitter and Mastodon.
Safety Implications of Autonomous Vehicle Technologies: A Comprehensive Analysis of Self-Driving Cars
The emergence of autonomous vehicle technologies represents one of the most significant transformations in transportation history. As we stand on the cusp of this revolutionary change, it’s crucial to examine the safety implications that come with the integration of self-driving vehicles into our daily lives. This comprehensive analysis delves into the various aspects of autonomous vehicle safety, exploring both the promises and challenges that lie ahead.
Upcoming Apple Products 2024: A Game-Changing Lineup Reshaping the Tech Landscape
As we delve into the exciting world of upcoming Apple products, it’s crucial to understand how these innovations are poised to reshape not just the technology landscape but the entire global market. Apple’s consistent ability to drive industry trends and set new standards makes their upcoming releases particularly significant for consumers, investors, and competitors alike.
Future of Mobile Apps: Predicted Trends in App Popularity and User Engagement for 2025
As we approach 2025, the mobile app ecosystem is undergoing a dramatic transformation, driven by technological advancements, changing user behaviors, and evolving market demands. This comprehensive analysis explores the anticipated trends that will shape app popularity and user engagement in 2025, providing valuable insights for developers, businesses, and tech enthusiasts.
Can Hacking Help Identify Vulnerabilities in Blockchain Technology?
The rapid growth of blockchain technology has revolutionized various industries by providing decentralized and secure solutions. However, like any technology, blockchain systems are not immune to vulnerabilities. This raises an important question: Can hacking help identify vulnerabilities in blockchain technology? This article delves into how hacking, particularly ethical hacking, plays a crucial role in uncovering and addressing potential security flaws in blockchain systems.
How Hackers Manipulate APIs for Unauthorized Access: Techniques and Prevention
Application Programming Interfaces (APIs) have become the backbone of modern software development, enabling seamless communication between different systems and services. While APIs offer numerous benefits, they also present potential vulnerabilities that hackers can exploit to gain unauthorized access. Understanding how hackers manipulate APIs is crucial for organizations to implement robust security measures and safeguard their digital assets.
What do I do if my adapter’s resolution doesn’t match my monitor?
When you connect a monitor to a computer or laptop using an adapter, it’s essential that both devices support compatible resolutions. If the resolution of your adapter doesn’t match your monitor, you might experience issues such as blurry images, distorted graphics, or even a blank screen. Here’s what you can do to troubleshoot and resolve these issues.
How Artificial Intelligence is Revolutionizing Cybersecurity: Advanced Protection Against Modern Threats
In today’s rapidly evolving digital landscape, cybersecurity threats have become increasingly sophisticated and challenging to detect. Artificial Intelligence (AI) has emerged as a game-changing technology in the fight against cybercrime, offering unprecedented capabilities in threat detection, prevention, and response. This comprehensive guide explores how AI is revolutionizing cybersecurity and helping organizations stay one step ahead of potential breaches.
How AI is Revolutionizing Real-Time Language Translation: Breaking Down Global Communication Barriers
In recent years, artificial intelligence has dramatically transformed the landscape of real-time language translation, ushering in an era of unprecedented global communication. This technological revolution has made it possible for people worldwide to connect, collaborate, and understand each other instantly, regardless of language barriers.
How to Download YouTube Videos: Complete Guide for 2024
Downloading videos from YouTube can be essential for various purposes, from offline viewing to educational use. This comprehensive guide will walk you through different methods, tools, and important considerations for downloading YouTube content safely and effectively.
The Role of AI in Climate Change Solutions
As the world faces the looming threat of climate change, innovative solutions are more crucial than ever. Among these solutions, Artificial Intelligence (AI) stands out as a transformative tool that can greatly enhance efforts to combat climate change. By leveraging vast amounts of data, AI can optimize processes, improve predictive models, and facilitate more efficient systems across various sectors. This article delves into the multifaceted roles AI plays in addressing climate change solutions.
Do USB Hubs Work With Both Mac and Windows Computers?
As technology continues to evolve, the need for versatile and efficient connectivity solutions has grown significantly. One of the most practical devices for achieving this is the USB hub. USB hubs allow users to connect multiple devices to a single USB port, enhancing productivity and making it easier to manage peripherals. However, many users often wonder: do USB hubs work with both Mac and Windows computers? In this article, we will explore the compatibility of USB hubs with Mac and Windows systems, examine different types of USB hubs, and provide valuable insights into their features and performance.
The Evolution of Augmented Reality and Virtual Reality: What’s Next?
The realms of Augmented Reality (AR) and Virtual Reality (VR) have seen tremendous growth and innovation over the past few decades. These technologies have transitioned from being mere concepts in science fiction to becoming integral parts of various industries, including gaming, healthcare, education, and more.
The Role of Blockchain Beyond Cryptocurrency
Blockchain technology is often synonymous with cryptocurrency, but its potential extends far beyond digital currencies. This burgeoning technology offers robust solutions across various sectors, promising enhanced security, transparency, and efficiency.
What is the Maximum Power Output of a USB Hub?
In today’s digital age, USB hubs serve as essential devices enabling users to connect multiple peripherals to a single USB port on their computers or laptops. Understanding the maximum power output of a USB hub is crucial for ensuring that all connected devices operate efficiently and effectively. This article explores the specifications, standard power outputs, types of USB hubs, and other relevant details that will help users maximize their connectivity options.
How Cloud Computing Is Changing the Way Businesses Operate
In recent years, cloud computing has revolutionized the way businesses operate, offering a myriad of benefits that range from increased efficiency to cost savings. In this article, we will explore how cloud computing is transforming various aspects of modern business operations.
The Rise of Quantum Computing: How It Could Change the World
Quantum computing is an emerging field that leverages the principles of quantum mechanics to process information in ways that classical computers cannot. This groundbreaking technology promises to revolutionize numerous industries by solving complex problems more efficiently than ever before.
The Complete Guide to Saving Instagram Stories for Future Reference
Instagram Stories have become an essential way to share moments with friends, family, and followers. However, these stories disappear after 24 hours, leaving many users wondering how to save them for future reference. This guide will walk you through various methods and tools to effectively save Instagram Stories.
Mastering Connections Hint 16: Comprehensive Guide to Effective Networking
In the competitive world of business and networking, mastering effective strategies is crucial. One such strategy is Connections Hint 16, a powerful tool that can significantly enhance your professional network.
How Do I Stream in HD Using My Webcam?
Streaming in HD using your webcam can significantly enhance the quality of your broadcasts, whether you’re a gamer, a content creator, or someone who hosts webinars. To ensure you achieve high-definition quality, you need to follow several essential steps, tweak some settings, and might need additional tools. This comprehensive guide will walk you through the process.
How to Download a TikTok Video: An Easy Guide
If you are looking to download a TikTok video, you have come to the right place. SnapTik is your go-to online service for easily downloading high-quality TikTok videos directly to your device.
Best PS5 Headset: Elevate Your Gaming Experience
As a gamer, immersing yourself in the world of PlayStation 5 requires not just stunning graphics, but also impeccable audio quality. Finding the best PS5 headset is crucial to enhance your overall gaming experience, providing you with crystal-clear sound, superior comfort, and features that can give you a competitive edge.
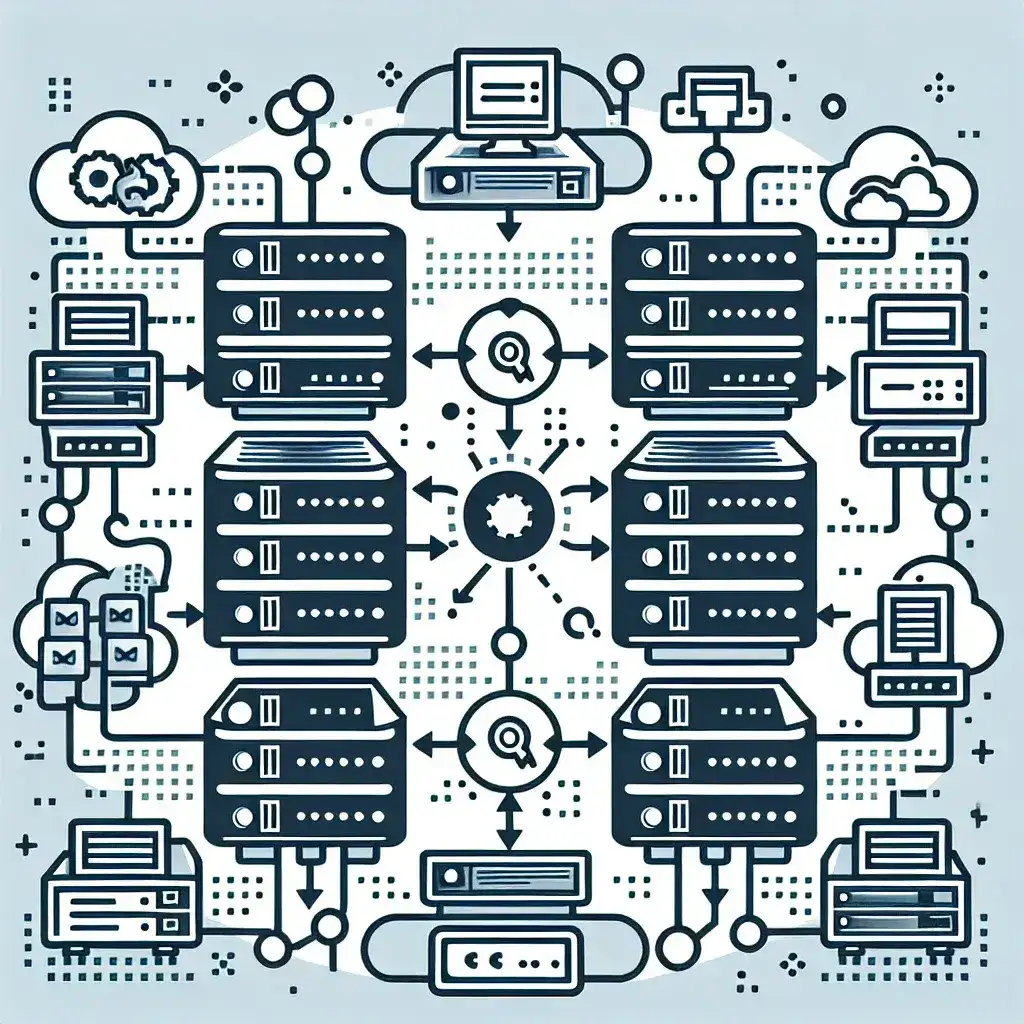
How is server maintenance handled in shared hosting?
Shared hosting is a popular and cost-effective web hosting solution where multiple websites reside on a single server. The resources of the server are shared among numerous users, making it an ideal choice for small to medium-sized businesses, blogs, and personal websites. However, with shared resources comes the critical aspect of server maintenance. Understanding how server maintenance is handled in shared hosting is crucial for ensuring the optimal performance and security of hosted websites.
What are shared hosting server clusters?
In recent years, the online presence of businesses and individuals alike has become paramount. One critical aspect of maintaining a robust online presence is ensuring that your website is fast, reliable, and always accessible. This is where shared hosting server clusters come into play. But what exactly are they, and how do they benefit your online endeavors?
What happens if one website on shared hosting uses too many resources?
Shared hosting is a popular choice for small to medium-sized websites due to its affordability and ease of management. However, one of the main drawbacks is the shared nature of resources among multiple websites on the same server. This arrangement can lead to significant issues when one website begins to consume an excessive amount of resources.
How do you set up a modem for a large office network?
Creating a robust and reliable network in a large office setting is crucial for productivity and communication. This guide provides step-by-step instructions on how to set up a modem for a large office network. With the right approach, you’ll ensure your network’s efficiency, security, and scalability.
Can LCD Monitors Be Wall-Mounted?
With the rise in popularity of sleek and space-saving solutions, many people wonder: Can LCD monitors be wall-mounted? The answer is a resounding yes. Wall-mounting an LCD monitor can not only enhance the aesthetic appeal of a room but also free up valuable desk space and improve ergonomics. This article delves into the benefits, methods, and important factors to consider when wall-mounting an LCD monitor.
What is the best way to extend a modem’s Wi-Fi range?
Wi-Fi is essential for modern living, yet many of us continue to struggle with weak signals and dead spots in our homes or offices. Different factors such as physical obstructions, interference, and the router’s placement can heavily influence Wi-Fi performance. To effectively extend a modem’s Wi-Fi range, it’s crucial to identify the root cause of the issue.
What is IPS technology in LCD monitors?
In the realm of display technology, IPS (In-Plane Switching) stands out as a notable advancement, particularly in the context of LCD monitors. This technology, which was pioneered by Hitachi in the mid-1990s, has since become a cornerstone for high-quality display screens, offering users superior color accuracy, wider viewing angles, and overall better performance compared to its counterparts. This article delves into the intricacies of IPS technology, outlining its benefits, applications, and its comparison with other display technologies.
How do you optimize a modem for low-latency applications?
Low-latency applications require minimal delay in data transmission to function effectively. Examples include online gaming, video conferencing, VoIP calls, and real-time financial trading platforms. Optimizing your modem for low latency can significantly enhance your user experience in these scenarios.
Are LCD monitors prone to screen burn-in?
Understanding the susceptibility of LCD monitors to screen burn-in is crucial in today’s digital age where monitors are a primary medium of information consumption and media enjoyment. While screen burn-in is a well-known issue associated mostly with older CRT and plasma displays, consumers often question whether modern LCD monitors face the same problem.
How do laptops with hardware-level voice assistants differ from software-based ones?
Voice assistants have become integral to modern computing, offering convenience through hands-free operation. These assistants come in two primary types on laptops: hardware-level and software-based. Understanding the distinctions between these types can guide consumers in making informed purchasing decisions.
Why might a laptop have a built-in light meter or colorimeter?
In the rapidly evolving landscape of technology, laptops are becoming more advanced and feature-rich. Among the sophisticated technologies embedded in modern laptops, built-in light meters and colorimeters have been gaining popularity. But why might a laptop have these features? In this article, we’ll delve into the purposes and benefits of having a light meter or colorimeter in your laptop.
What makes a laptop ideal for professional color grading and HDR work?
The world of professional color grading and HDR (High Dynamic Range) work requires a powerful and reliable laptop that can handle the intensive demands of editing high-resolution videos and images. This article delves into the key features and specifications that make a laptop ideal for these tasks.
Master the Art of Email Marketing: Tips for Success
Email marketing remains one of the most effective digital marketing strategies. To leverage its full potential, you need to master the art. This comprehensive guide will walk you through the essential tips for email marketing success.
Instagram Story Viewer
Instagram has quickly become one of the most popular social media platforms, largely due to its engaging features like stories. An essential part of this experience is the AnonyIG Instagram Story Viewer. Understanding how it works, its features, and leveraging it to the fullest can significantly enhance your social media presence.
How do I choose the right headphones for different purposes?
Headphones have become an essential part of our daily lives. Whether you use them for listening to music, gaming, working out, or professional purposes, choosing the right pair can significantly impact your experience. With so many options on the market, it’s crucial to understand what to look for in headphones that best suit your needs.
Use Social Media for Networking and Career Advancement
In today’s digital era, social media has become an indispensable tool for networking and career advancement. By strategically using platforms like LinkedIn, Twitter, and even Facebook, professionals can build valuable connections, showcase their expertise, and open doors to new opportunities.
What are common causes of audio distortion and how can I fix them?
Audio distortion can be a frustrating issue, particularly when you are aiming for pristine sound quality. Understanding the common causes of audio distortion and knowing how to fix them is crucial for anyone involved in audio production or simply looking to enhance their listening experience.
Grow Your Social Media Following Organically
Building a loyal social media following is essential for personal branding, businesses, and influencers alike. However, achieving this organically requires more than just posting content. This article will guide you through effective strategies to grow your social media following organically.
Create Engaging Content: Tips for Writing Captivating Posts
In today's digital landscape, creating engaging content is crucial for capturing your audience's attention. Whether you're a blogger, marketer, or business owner, crafting captivating posts can lead to increased traffic and higher engagement. Here are some practical tips to help you write content that resonates with your readers.
Boost Productivity: How to Easily Edit PDF Documents Online
In today’s digital age, the ability to edit PDF documents swiftly is essential for productivity. Whether you are managing contracts, reports, or academic papers, having a reliable and efficient tool to modify PDF files is crucial. Let’s explore the best platform that offers a seamless PDF editing experience.
How do I set up an audio streaming server?
Setting up an audio streaming server can seem like a daunting task at first, but with the right guidance and tools, it can be an enjoyable and rewarding experience. This comprehensive guide will take you through the steps necessary to set up your very own audio streaming server.
3 Simple Ways to Create a Home Network
Creating a home network has become essential in modern households, enabling multiple devices to share internet access, files, and printers efficiently. Below, we explore three simple ways to establish a home network, suitable for varying levels of expertise and requirements.
How to Disable Windows 7 Firewall?
The Windows 7 Firewall is an essential feature that helps secure your computer from unauthorized access and potential threats. However, there are times when you might need to disable the firewall temporarily or permanently for various reasons, such as troubleshooting a network issue or using third-party security software. This guide will provide detailed steps on how to disable the Windows 7 Firewall effectively.
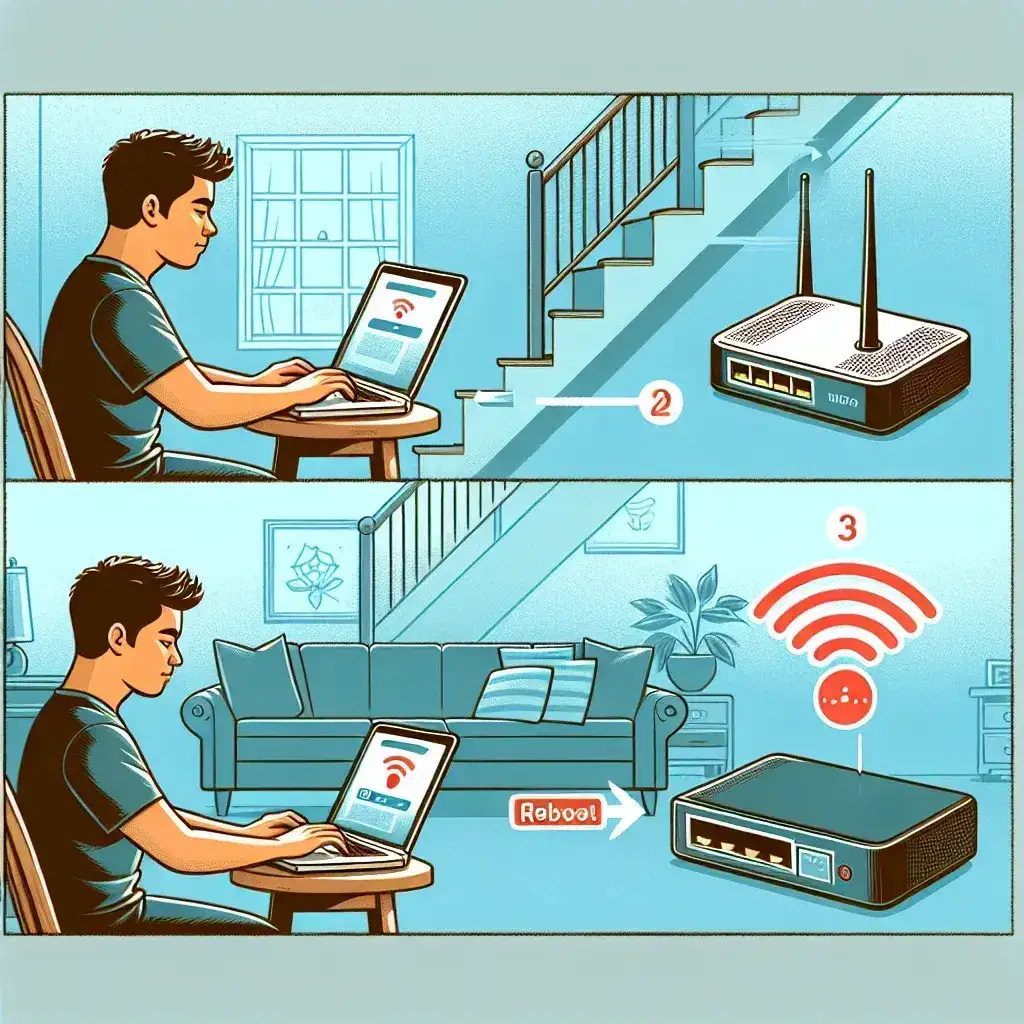
How to Reboot a DSL Modem Remotely?
Rebooting a DSL modem remotely can be a lifesaver when you’re experiencing connectivity issues and you’re not physically near the device. Whether you’re traveling, taking care of a remote office, or simply upstairs and too lazy to descend, knowing how to reboot your modem from afar is a valuable skill. In this article, we’ll guide you through the process, ensuring you have a seamless experience.
Everything You Need to Know About Connecting to a VPN
In today’s digital age, privacy and security are of utmost importance. Connecting to a Virtual Private Network (VPN) is a fundamental step to protect your online activities from prying eyes. Whether you’re a seasoned tech enthusiast or a complete beginner, this guide provides everything you need to know about connecting to a VPN.
How to Download Instagram Videos: Your Comprehensive Guide
Instagram is one of the most popular social media platforms worldwide, boasting millions of users who share photos, videos, and stories daily. Sometimes, you come across a video that you absolutely love and want to save for later. This article will guide you on how to download Instagram videos quickly and easily.
What Color Airpods Do You Want?
When it comes to choosing the perfect pair of AirPods, one of the most exciting aspects is the ability to select a color that matches your style. While Apple’s default offerings have been limited, a number of custom solutions now make it possible to have AirPods in virtually any color you desire. But what factors should you consider when selecting the right color for your AirPods?
How Much RAM Do You Need?
When it comes to computing, Random Access Memory (RAM) plays a pivotal role in determining the speed and efficiency of your activities. Whether you are a casual user, a gamer, or a professional working with resource-intensive applications, understanding how much RAM you need can make all the difference. This guide will help you understand what RAM is, the different amounts of RAM required for specific tasks, and how to determine the RAM requirement for your needs.
How to Configure a Laptop to a Wireless Router?
In today’s digital world, having stable and reliable internet connectivity is indispensable. Whether for work, study, or entertainment, configuring your laptop to a wireless router efficiently can make a significant difference in your online experience. This guide will walk you through step-by-step instructions to ensure you get connected without any hitches.
How to Connect a Headset to a PC?
Connecting a headset to your PC is a straightforward process, whether you are using a wired or wireless headset. Having a good quality headset can enhance your audio experience whether you are gaming, working, or just enjoying some music. This guide will walk you through the steps to connect your headset correctly and troubleshoot common issues you might encounter.
Faxing from a Printer & Alternatives
In today's digital age, the concept of faxing may seem archaic; however, many businesses still rely on this method for secure communication. This article will guide you through faxing from a printer and explore modern alternatives.
How to Change the Default Media Player on a Mac
Always wanted to switch from the default QuickTime player on your Mac to another media player? You are not alone. Changing the default media player can enhance your media-viewing experience significantly. This guide will walk you through the steps to change your default media player seamlessly.
Agile Development: Collaborative Flexibility
Agile development prioritizes collaboration, flexibility, and iterative progress in software development. By fostering close communication between teams and stakeholders, Agile methodologies enable quicker responses to changing requirements and market demands. This article discusses the core principles and benefits of Agile development, offering insights into how it can improve project outcomes and customer satisfaction.
End-to-End Encryption: Data Transmission Security
End-to-end encryption ensures secure data transmission by encoding data at the sender’s end and decoding it at the recipient’s end. This method protects data from unauthorized access during transmission, enhancing privacy and confidentiality. The article explores the significance of end-to-end encryption, its applications, and how it contributes to secure communication and data protection.
Network Analysis: Intrusion Detection
Effective network analysis is essential for identifying and preventing security breaches. Intrusion detection systems (IDS) monitor network traffic for suspicious activity, allowing organizations to take proactive measures. This article explores the importance of network analysis in safeguarding data, discussing various IDS methods and best practices for detecting and mitigating potential threats.
Effortlessly Download YouTube Videos with SSYouTube
In today’s digital age, downloading YouTube videos has become increasingly necessary for offline viewing. The YouTube video download app SSYouTube simplifies this process, allowing users to download videos quickly and efficiently. Whether you want to save educational content, music videos, or tutorials, SSYouTube makes it hassle-free.
Easy Instagram Clip Download
Downloading Instagram clips can be straightforward with the right methods. This article guides you through simple and efficient ways to instagram real download, allowing you to enjoy your favorite content offline or share it with others. Discover user-friendly techniques to streamline your Instagram experience and keep up with the latest trends.
Snapchat AI Stories: Next-Gen Social
Get ready to be amazed! Social media is on the cusp of a transformative leap, and Snapchat is leading the charge with AI-powered Stories. Imagine personalized narratives that adapt to your mood, curate content you crave, and even predict your next move. This isn’t science fiction; it’s the future of social interaction, unfolding right before your eyes.